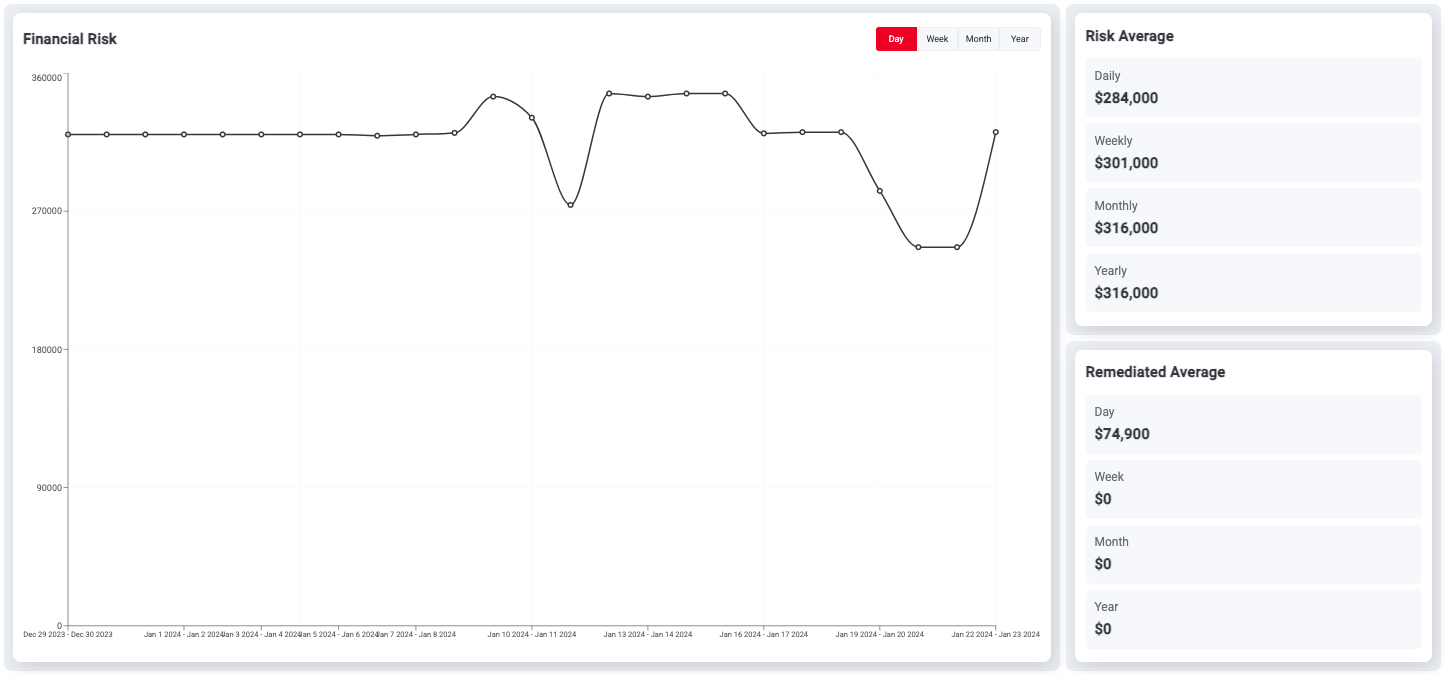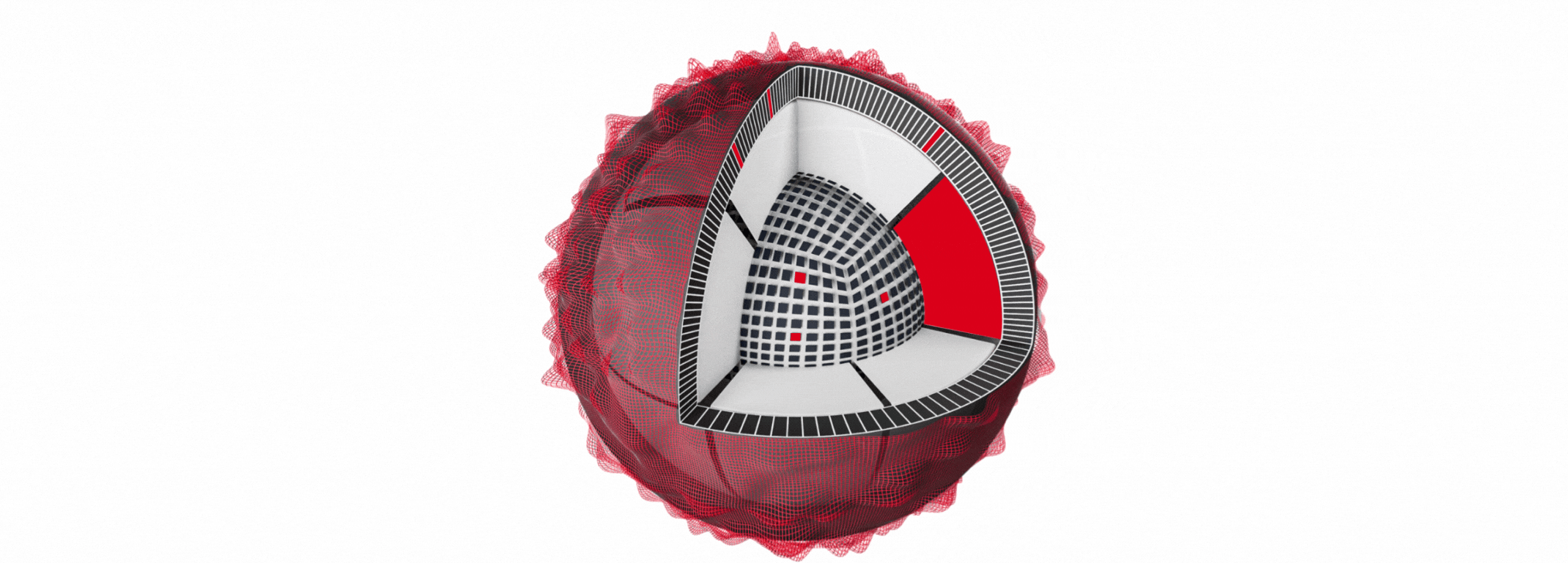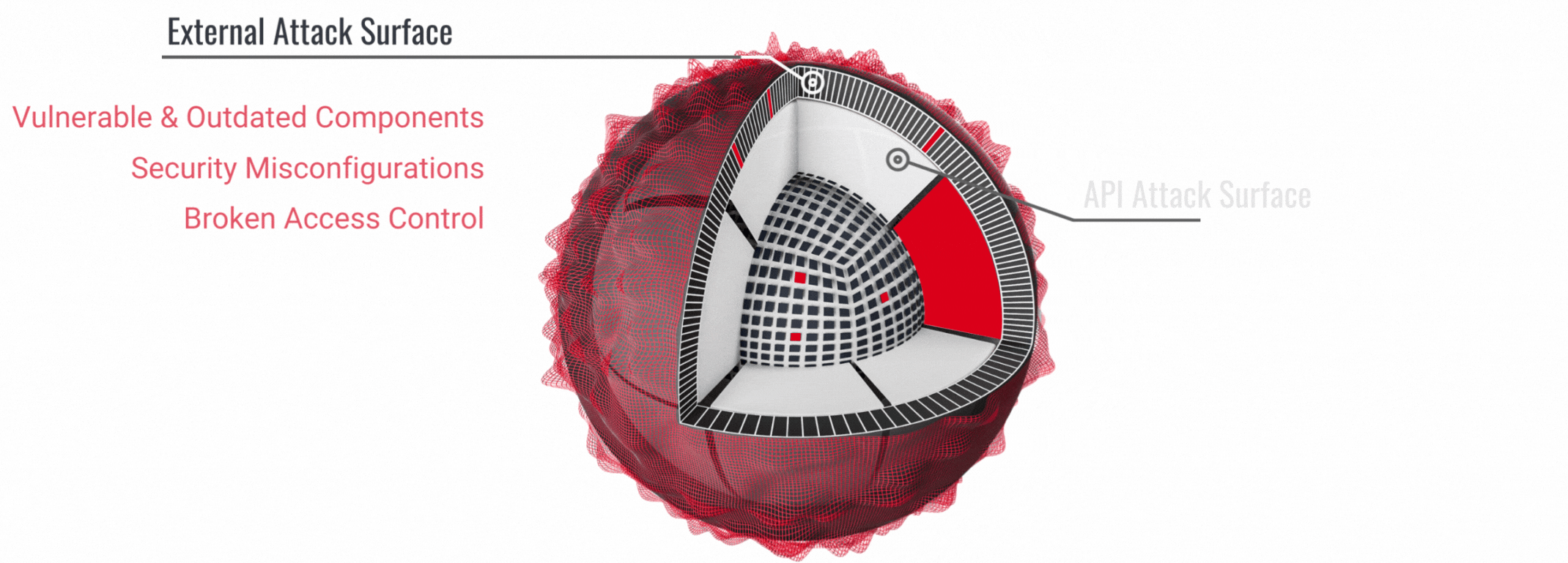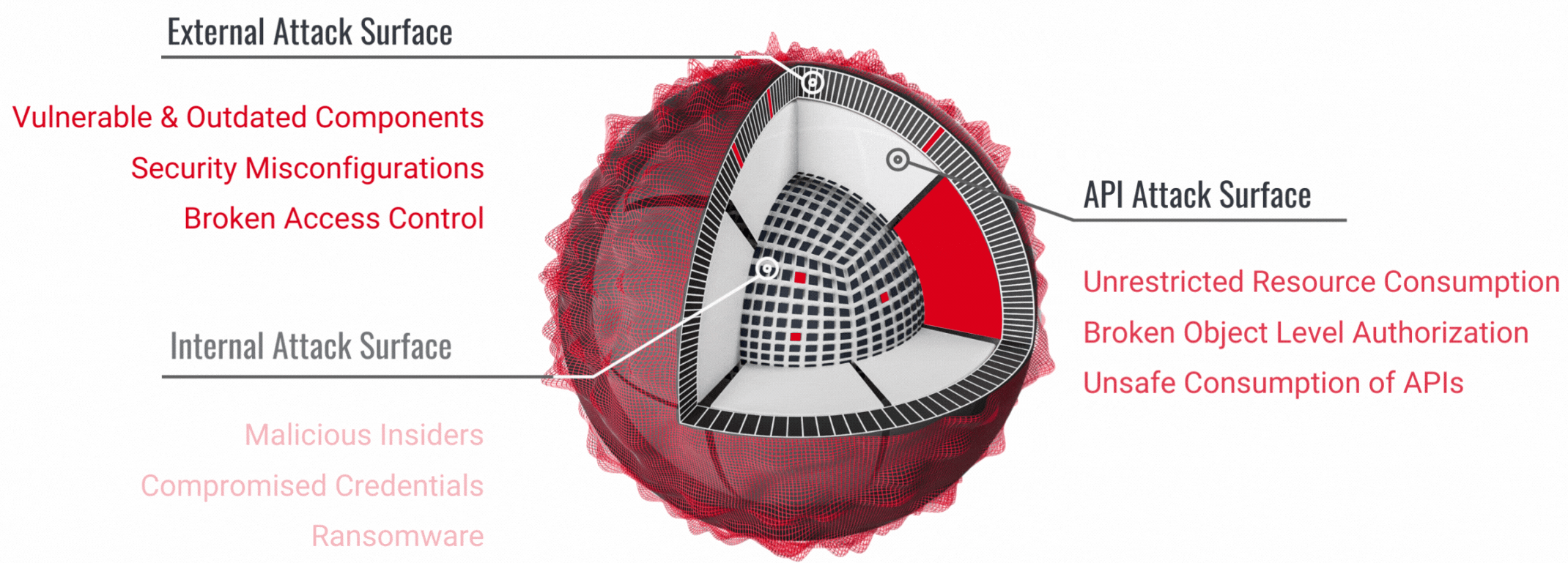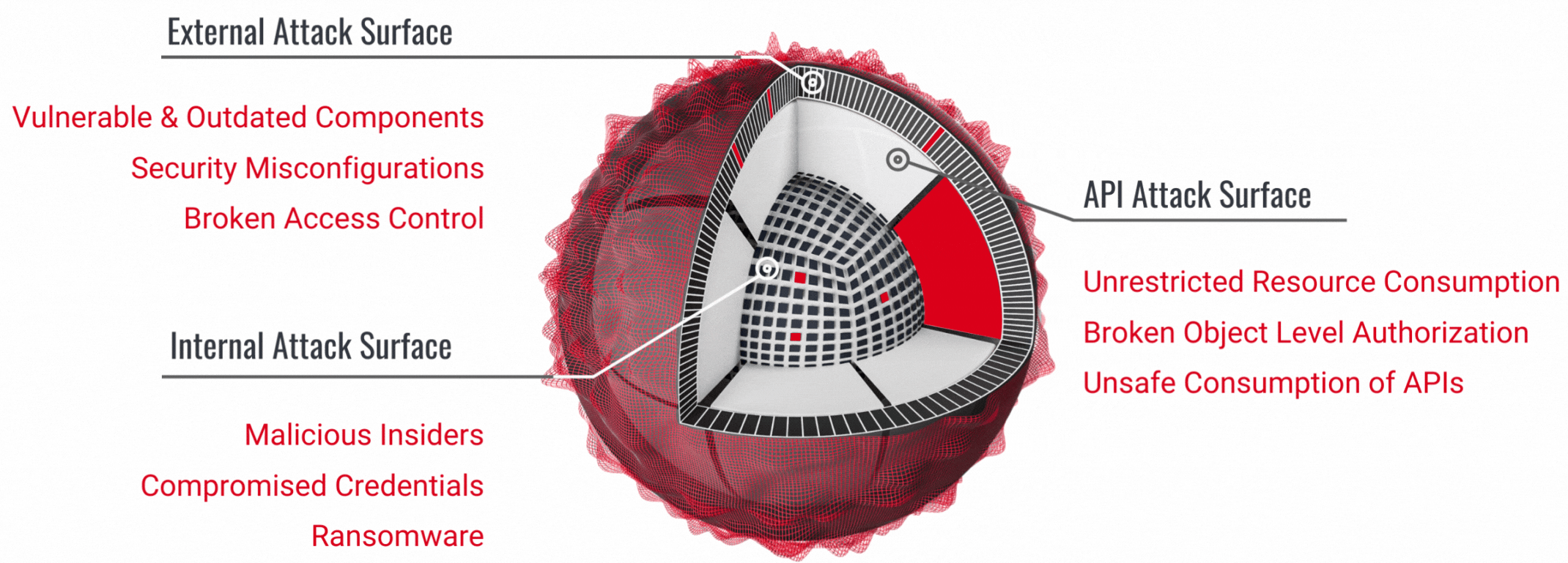

Protect Yourself from Black Friday Online Threats: Pro Tips to Stay Safe
Discover essential tips to protect yourself from phishing, fake websites, and other online threats this Black Friday week. Learn how to spot scams, shop securely, and respond if you fall victim. Don’t let cybercriminals ruin your holiday shopping - stay informed and shop smart!
Read Article